EZ MSP Blog
These days, data privacy is absolutely critical in both a business and individual context. In some locations, governments have introduced legislation to protect consumers, and in others, there is significant pushback in favor of fewer regulations on business. How does data privacy factor into your business’ operations?
In 2004, a service called VirusTotal was launched and swiftly became a popular antivirus and malware scanner to help detect threats in various files and URLs. It became popular enough that it was officially acquired by Google in 2012 and ultimately assimilated into Chronicle, a cloud-based security operations suite for enterprise businesses. Despite this impressive pedigree, however, we find ourselves able to look to VirusTotal as a sobering reminder of how fickle cybersecurity can be, with the service being the source of some limited data exposure.
Compliance is a critical element of many businesses’ requirements, with pretty severe penalties as a consequence if the prescribed standards are not met. Even more importantly, most compliance requirements and regulations are put in place for the welfare of not only the business, but its clientele as well. This makes it critical to know which apply to your business, and how to meet them fully.
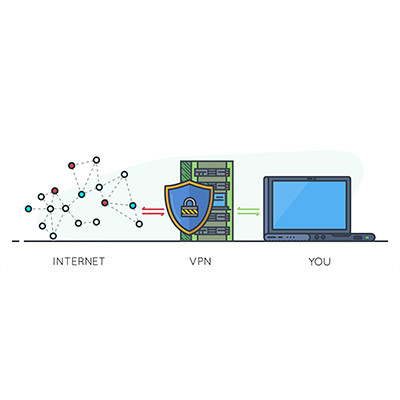
When it comes to security, one often overlooked tool is the virtual private network, or VPN. We recommend that all businesses use a VPN to keep remote and hybrid workers from inadvertently putting your business’ data at risk while out of the office. Let’s go over why a VPN is so effective, as well as what you should look for in a business-grade VPN tool.
Who are you? While it’s a question that’s been asked in all contexts with all levels of metaphysicality attached—from asking someone their name to prompting someone to follow a path of spiritual self-discovery—the growth of the metaverse once again urges us to ask it in a more literal way. When accessing a conglomeration of various services and platforms, how many identities will each user need to juggle?
We aren’t going to try and pretend that the investments necessary to preserve your business’ data security are small ones. Especially at first glance, you may very well start to question if such an investment is truly necessary.
The simple fact of the matter is that, compared to the costs that a breach of privacy will incur, the investment you put into your security measures will suddenly seem like a real bargain.
Chances are, you’ve gone through some old files and weeded through them, deleting what is no longer needed. This is especially important when you are upgrading your storage and getting rid of your existing storage media or an old computer. Let’s talk about what really happens when you’re doing so—chances are, you may be overlooking a serious security issue.
Have you ever wondered how some platforms will only have you log in once for all of your various needs, even though they might be different applications, websites, or services? This is essentially what single sign-on is, and it’s quite common in the technology world today. What is single sign-on exactly, and what kind of security does it actually provide for organizations that use it?
When we talk about data privacy in a business, the default is to generally think about the data the business has collected and compiled from its clientele. However, that’s just one type of data a business has. There’s also a lot of data that is collected by the business about that business’ employees. So, how well protected is this data?
With so many employees still working remotely, organizations have turned to technology to ensure that their workers are actually… you know, working. While the need to know what your employees are up to throughout the workday is important, there is now a discussion happening on whether or not this violates employees’ privacy.
Most businesses have compliance regulations they need to meet. 2021 is becoming somewhat of a tipping point for some. Companies are dealing with the development of new data privacy laws that will surely add some responsibilities on top of already established regulations. This month, we thought we’d take a look at compliance and why it is important to stay on top of it.
With many—if not most—computers and especially laptops featuring integrated webcams at this point, it isn’t hard to imagine how disastrous it would be to be spied on through it. Let’s take a few moments and go over a few ways to be sure that your webcam isn’t being used without your consent by someone else.
Facebook is many people’s favorite—or at least most used—app and it does bring value to people by letting them keep tabs on friends and family, or grow their businesses. It has grown to be one of the largest, most successful software technology companies in the world. Unfortunately, with that type of exposure comes the responsibility of securing massive amounts of personal data. In this quest, they leave a lot to be decided. Today, we take a look at the situation Facebook is in as they are dealing with one of the largest data leaks in history.
We’re getting close to the end of 2020. Finally? Has it been a long year for you? Has it gone by really fast? I think every other day I have a different opinion about it.
Either way, it’s time to look at 2021. A fresh start, a clean slate. I think if there is one big mindset all business owners and C-levels need to take into consideration for 2021, it’s their people.
Keeping your network and infrastructure free from threats is always a priority, but with so many people working remotely, businesses have encountered problems doing so. In fact, hackers and scammers have come out of the woodwork to try and gain entry into unauthorized networks or to flat-out steal data. This month, we thought we would take a look at how the COVID-19 pandemic has exacerbated the threats out there.
Security is a major part of any business, and if there isn’t a diligent approach to the implementation of it, you can be left with huge holes in your network. This month, we thought we would discuss some of the best practices you can take to make sure that your organization’s security is in the best possible position to protect your digital resources.
Smart assistants commonly appear in the office and home, so much so that the novelty seems to have finally worn off and they are now just another appliance—and, like any other appliance, there are a few quirks that can be frustrating to deal with. For instance, anyone living around these devices has shared a particular experience: the device registering something as a wake word that certainly wasn’t meant to be the wake word.
What if I were to tell you that, by the time you finished reading this sentence, all personal data in existence was exposed? If every text sent, every Google search executed, every website visited, everything we had ever done online, was made public? Gizmodo recently reached out to an assortment of experts for their insights. Here, we’ve assembled their responses for you to consider.